Uninterrupted, real-time web security
Web Server Safeguard, or WSS, is UMV’s pioneering product, trusted by hundreds of global companies and institutions to enhance their web server security
In an age where cyberattacks are evolving by the day, even small delays in response can lead to devastating breaches
Malware constantly refined to exploit new vulnerabilities in network systems
Many security systems aren’t protected from attacks both inside and outside the organization
Ineffective exception processing in a cybersecurity of encoded scripts lets damaging malware through
Further risk posed by malware that’s parsed, hidden, and/or encrypted
Malicious scripts planted before firewalls have been set up go undetected
Other security incidents like exploiting network bypass vulnerabilities or overloads can also result in infiltration




WSS defends web servers from a variety of web attacks such as APT attacks, ransomware, attacks using web shell uploads, and website spoofing attacks.
Using functions such as detection, monitoring, quarantine, and reporting, WSS stops web shells before they can do any damage.
With WARSS, UMV’s security solution customized for websites, you can also prevent website defacement, source code forgery, and content forgery with ease.
WARSS detects changes to your homepage and restores it to its original state in real-time, making sure your website never misses a beat.
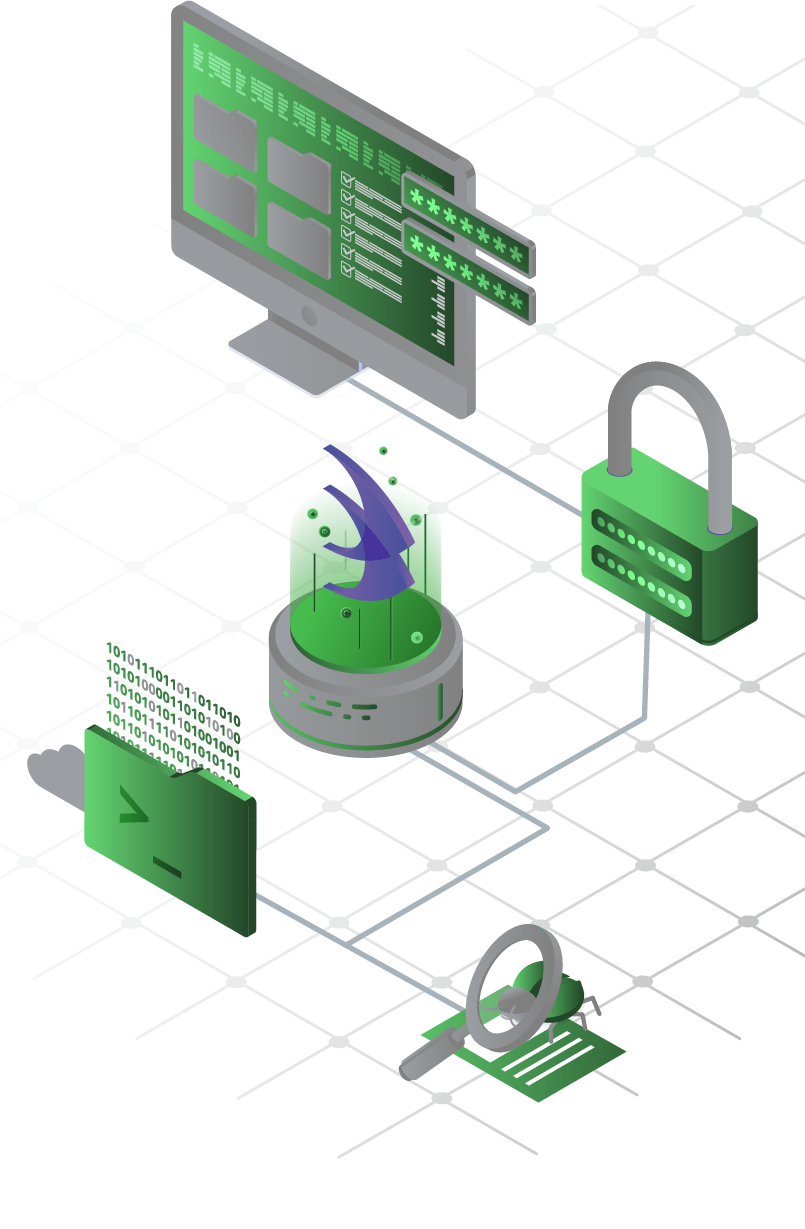
To improve detection,
unknown malicious code is collected and detected
through WSS’s dedicated obfuscation analysis engine, SCR Parser.
Detect patterns stored in the DB via comparison with intrusive files
Generate and inspect signatures of well-known web shells
WSS’s dedicated SCR Parser detects patterns like obfuscated JavaScript webshells
Regularly save and update web shell hash values as published on VirusTotal
Security booster solution for webservers, protecting information data and providing uninterrupted service