
Web Server & Cloud Computing Security Solution
WARSS
Website Attack Restoration Security Solution:
Real-time website forgery detection and recovery

Website Hacking
Threat actors, taking advantage of various weaknesses in information systems, gain access to a system and launch attacks such as webpage defacement, changing web server source code, data forgery, and/or modifying website content (e.g. image files and videos).
Homepage Forgery:
Attack Vectors
- Exploitation of network security solution weaknesses
- Exploitation of source and file upload vulnerabilities
- Malicious activity of members inside the organization (e.g. internal and external partners)
- Exploitation of OS web server/WAS Zero Day vulnerabilities


Website attack restoration security solution
Real-Time Web Security Solution
WARSS provides comprehensive and real-time security against website attacks, setting it apart from other methods like web crawling.
WARSS for Cloud
Scale In/Out
Automate detection and registration of detection targets when a web server or WAS is scaled
History Management
View and manage Agent statuses and operation history (installations, pausing, etc.)
Home Directory Detection
Auto-detect and schedule WEB/WAS home directory changes or additions; automatically search for home directories
Event Duplication Management
Prevent duplicate detection events; detected events transmitted in real time
WARSS Operation Diagram
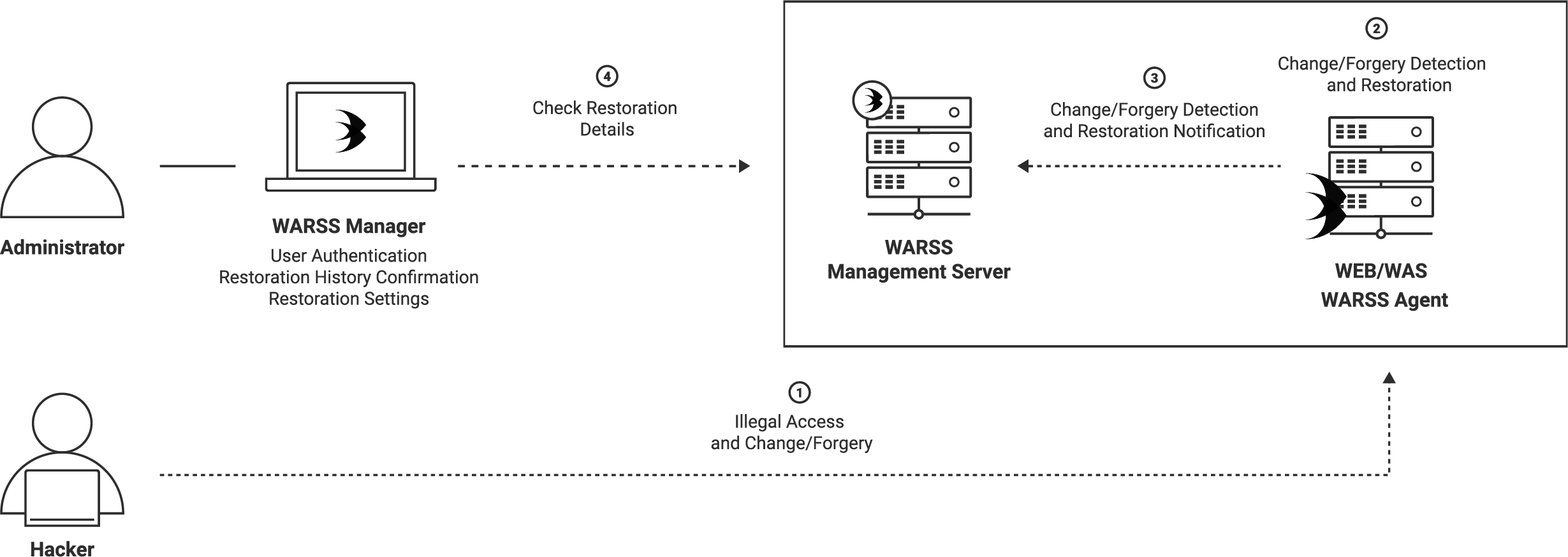

Secure Your Website in Real-Time with WARSS
When WARSS (Website Attack Restoration Security Solution) detects changes to a website’s contents, it restores them back to their original files in real-time
WHY CHOOSE UMV?
17 Years of Experience
WARSS is the only solution in Korea capable of blocking defacement attacks in real-time, even during active hacking attempts. In other words, it functions as a real-time website security solution. Recently, it has been successfully deployed in high-security environments that require continuous monitoring, such as KOICA’s export project in Algeria and top-level government institutions, delivering excellent results.
Trust
For 17 years, we have maintained a flawless track record since implementation, fostering strong relationships with our initial customers and expanding the system. Notable clients include Samsung, Hyundai Card, and NongHyup Bank.
Excellence
WARSS is the only solution in Korea capable of blocking defacement attacks in real-time, even during active hacking attempts. In other words, it functions as a real-time website security solution. Recently, it has been successfully deployed in high-security environments that require continuous monitoring, such as KOICA’s export project in Algeria and top-level government institutions, delivering excellent results.
Stability
WARSS is designed to minimize CPU and memory usage on the target server, ensuring low resource consumption. It provides high portability across all operating systems that support Java 1.5 or higher, including Windows, Linux, and Unix. The management server also supports high availability (HA) through a dual configuration, enabling stable and reliable service operation.
Testimonials

“…At first, I thought website security was just about blocking attacks, but WARSS turned out to be much more. It continuously monitors all web content files—like source code, images, and videos—and instantly restores the original files whenever any tampering is detected. The real-time monitoring and automatic recovery give me peace of mind as a website administrator…..”
KOROAD

“…Since we run our services in a cloud environment, instances are frequently added and removed. WARSS makes it really convenient by automatically registering or deregistering targets for monitoring as the environment changes. The logs are well-organized, and events are collected cleanly without duplication, which makes integration with our security monitoring system seamless and highly compatible….”
Ahnlab

“…What I found most impressive as an administrator was the well-designed access control by user role, along with detailed usage logs and statistical reports. It made it easy to monitor the system at a glance, and important events were instantly delivered via SMS or email, which greatly improved our response time…..”
NH BANK
Explore Other UMV Products


What kind of web content can WARSS monitor?
WARSS can monitor and protect all website content, including source code, images, and videos.
Do WSS and WARSS have similar functions?
WSS and WARSS both strengthen web server/WAS security by performing detections in real-time.
WSS detects and quarantines web-based malware, whereas WARSS detects unauthorized additions/changes/deletions to web server/WAS source code files.
How does WARSS respond when an unauthorized change is detected in real-time?
When WARSS detects an unauthorized change to a web server file, the changed file is immediately restored to its original state from a stored backup. Notifications are also sent to an administrator, who can then compare the changed file with the original to analyze the attempted deletions, changes, and additions made to the file’s source code.
I already have multiple agents on my web server/WAS. Won’t adding another slow it down?
WARSS requires the installation of an Agent program onto each web server/WAS that needs to be protected. However, WARSS is extremely lightweight, and is designed to minimize resource usage (i.e. less than 1% CPU), ensuring that no impact is made to your web server/WAS’s normal functions.
How does WARSS compare to an agentless solution in terms of security?
Agentless anti-forgery solutions like scanners are almost always connected to the inernet through external networks. This means that the solutions themselves can introduce further security vulnerabilities to your network. On the other hand, all components of the WARSS system are fully internal, allowing you to retain the highest level of security for your server systems.
I already have a File Integrity Monitoring (FIM) solution. Do I need WARSS too?
File Integrity Monitoring (FIM) solutions protect the integrity of critical assets in file systems, directories, and system configurations by monitoring them for unauthorized or accidental modifications. Most FIMs alert an administrator when such a change is detected, and can offer limited mitigation functions as well.
However, WARSS goes one step beyond a traditional FIM to offer automatic, real-time file restoration. This ensures that any attempted change is immediately reverted back to its original state, and web services can continue uninterrupted.
Does WARSS offer integrations with other security management systems?
WARSS offers full integrations with many security management systems including ESM, SIEM, configuration management systems, and more. WARSS also supports integrations with SYSLOG, SMTP, API, SMS, e-mail, and more.
Are demos or PoCs available for WARSS?
Yes, we offer PoCs for WARSS. One of our engineers can help you get started and give you a run-down on its features. We can work with you to organize a PoC schedule and provide you with a checklist that allows you to see WARSS in action firsthand and learn how it will fit into your unique IT environment.
Contact us for more information on PoCs.
How much does WARSS cost?
WARSS is available under a variety of different licenses, which can be customized to the needs of our customers. Please contact us for more detailed pricing information.
