UMV Security Blog
Updates on web server security and web hacking from around the world
Search UMV’s website:
Kyowon Group Data Breach: 9.6M Leaked & Security Guide
Kyowon Group Data Breach: 9.6M Leaked & Security Guide The Kyowon Group Data Breach is a major security incident occurring in…
CISA Warns: Legacy PowerPoint and HPE OneView Exploits
On January 8, 2026, CISA expanded its Known Exploited Vulnerabilities (KEV) catalog. Specifically, they highlighted a dangerous trend where threat…
Amazon Uncovers Active Exploitation of Cisco and Citrix Zero-Days
Amazon detected an actor exploiting Cisco and Citrix zero-days. Read our analysis and response to protect your corporate networks. The Vulnerabilities CVE-2025-5777…
Japan’s New Cybersecurity Strategy: Active Defense Overview
On December 23, 2025, Japan’s Cabinet adopted a bold five-year cybersecurity strategy. It targets mounting cyber threats with proactive measures….
A Design Flaw in Microsoft’s .NET Framework
A heated debate is currently shaking the cybersecurity community. It involves a serious design flaw within Microsoft’s .NET framework. Since…
BrickStorm: The Stealthy Backdoor Hiding in US Tech Networks
A long‑running espionage campaign built around the BRICKSTORM backdoor has been quietly compromising US organizations since early 2025. The operators…
React2Shell Warning: Why Web Shells Drive APT Attacks
The 2021 Log4j crisis profoundly changed the global security landscape. Today, a new large-scale threat has emerged: the React2Shell vulnerability….
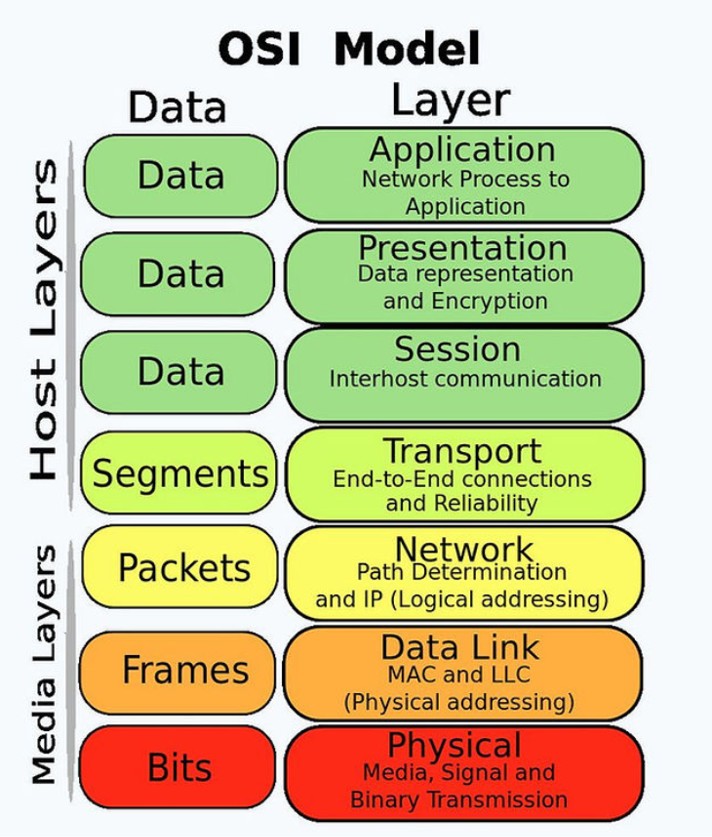
The OSI Model’s 7 Layers and Their Security Appliances
Imagine you’re sending a handwritten letter to a friend. First, you write it, then place it in an envelope, mail…
Godzilla Webshell: A Growing Cybersecurity Threat to Healthcare
The Health Sector Cybersecurity Coordination Center (HC3) has recently identified a cyber threat to the healthcare sector: Godzilla Webshell. What is…
The Rise of Cyberterrorism: A Growing Threat in an Unstable World
In recent years, the global security landscape has dramatically transformed as cyberspace emerges as a new frontier for warfare and…
ZERO TRUST: Are You Really Assuming Breach?
The modern cybersecurity landscape is constantly evolving, and the blurring of network permeters has given rise to increased interest in…
Digital Storm: Dawn Cavalry’s Cyber Assault on South Korean Institutions
As the Lunar New Year of 2023 approached, South Korea experienced an unexpected storm in the digital realm. The nation’s…
“The security chain is only as strong as its weakest link.”